All About Blockchain Security
What is blockchain security?
Today, we will be focusing more on how secure blockchain is, or in other words, blockchain security. Is Blockchain Secure? Vulnerabilities & Best Practices
Blockchain is generally considered a very secure network for storing data and recording transactions. However, hackers and scammers still find loopholes and make use of them to conduct malicious activities. In this article, we will be discussing about what is blockchain security, how hackers attack blockchain, and how a business can secure their blockchain network even more.
Why is blockchain ‘secure’?
The important motive of having a blockchain network is to establish a secure business network for storing data and recording transactions. It is considered secure because of its three important features: decentralization, consensus, and immutability.
Let’s understand them one by one…
Decentralization
Usually, a single authority never controls the entire blockchain network. The control is often decentralized and distributed over a network of computers (called nodes). This creates a transparent environment in which all the transactions are recorded in the ledger that is accessible to all. This helps to keep any manipulation in transactional data under check or in other words A blockchain is a shared ledger that works on a network of many computers. This setup means no single computer can control the whole system or change the records without others noticing.
Consensus
In blockchain, consensus is like a voting system for validating transactions. Only after a majority of the nodes agree (or vote) in favour, that the transaction is validated and tagged authentic. Blockchain uses systems like Proof of Work (PoW) and Proof of Stake (PoS) to confirm transactions. These systems make sure that participants agree on which transactions are valid, ensuring that only proper transactions get added to the blockchain.
Immutability
This aspect of blockchain further entails two more principles – cryptography and hashing. Cryptography, in simple words, is a method of securing transactions between two nodes using encryption and decryption.
Hashing is a way of detecting if any data has been altered or tampered with. It involves the use of hash, an alphanumeric digitized fingerprint that is unique to a block containing data. In a blockchain, a block contains the previous block’s hash in addition to its own. If any data in a block is altered, its hash value changes along with that of the following blocks. Cryptography and hashing together ensure that the data remains true and unchangeable.
Before moving to various kinds of blockchain cyberattacks and security measures, it’s crucial to understand the two types of blockchain network and how they differ.
Blockchain security and types of networks
Chainalysis defines blockchain security as “…the combination of cybersecurity principles, tools, and best practices in order to mitigate risk and avoid malicious attacks and unauthorized access while operating on blockchain networks.”
The security models and the kinds of vulnerabilities vary with the type of network – whether it’s public or private.
Public blockchain network
Public blockchain networks, as the name suggests, are open and permissionless networks that allow their members to remain anonymous. Anyone can join these networks and participate in validating transactions. They use the consensus mechanism to keep their network secure and transparent. Bitcoin is the most famous example of a public network where any member can validate new transactions in the form of mining and earn rewards.
No single authority or organization has complete control over these networks, thus, making them highly decentralized. However, there are groups of developers who constantly work to improve and secure the network. Other non-developer members also help with security by simply validating the transactions. Although decentralization ensures constant maintenance and improvement of the network, privacy is still an issue as everyone us allowed to read any transaction.
Private blockchain network
In contrast to public networks, private blockchain networks are controlled by a single authority that allows only known people to join them. Thus, its members are limited but verified. They are also faster and more efficient as they bypass the slow consensus mechanism used by the public network. While not all members may have access to the transaction ledger, some special members may enjoy privileges and exclusive rights.
The main problem with this network is its centralization – if the main authority faces any problem or malfunctions, it puts the rest of the network at risk too.
Types of blockchain cyberattacks
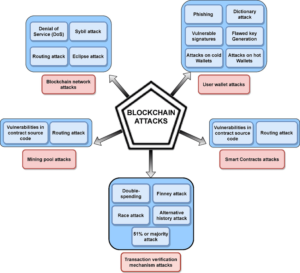
Image Credit:https://www.researchgate.net/figure/Different-types-of-attacks-on-blockchain_fig5_353073634
As you can see in the above image there are many types of blockchain cyber attack, but we are going to explain you major four types and these are: Sybil Attack, Phishing Attack, Routing Attack, Finney Attack. Fraudsters and hackers can attack the blockchain network in the following ways:
Sybil Attack
Sybil attack is about obtaining fake majority in a network to gain influence over it. Hackers gain this fake majority by operating multiple fake identities using a single node. These multiple identities are fake but appear real and authentic to other users. In other words, an attacker creates multiple fake identities to gain control over the network. This can disrupt the network’s operations and affect decision-making processes.
Phishing Attack
Phishing is when hackers try to obtain people’s personal and sensitive information through deception. Phishing is when attackers trick people into giving away sensitive information like private keys or passwords. They often do this by creating fake websites or sending emails that look like they’re from a legitimate source.
Routing Attack
These attacks occur at the network level. Attackers intercept data as it’s being transmitted, which can delay transactions or even cause them to fail, creating opportunities for double-spending or other malicious activities.
Finney Attack
A Finney attack is named after Hal Finney, one of the early contributors to Bitcoin. This attack takes advantage of the time delay between the broadcast of a transaction to the network and its confirmation. The attacker creates a transaction sending some cryptocurrency (let’s call it Bitcoin) from their wallet to another address they control. They do not broadcast this transaction to the network yet. The attacker then prepares to make a purchase with a merchant or someone who accepts Bitcoin. At the point of sale, the attacker makes a new transaction, paying the merchant with the same Bitcoin used in the first transaction. Immediately after this transaction is made, the attacker quickly broadcasts the first transaction to the network.











